Any third-party privilege access management (PAM) providers you wish to configure for use with Keyfactor Command must be defined first on the PAM Providers page before they can be assigned to certificate stores (see Certificate Stores), used for explicit credentials on a CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (see Adding or Modifying a CA Record), or used to provide authentication in workflow
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (see Adding or Modifying a CA Record), or used to provide authentication in workflow![]() A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. steps (see ). Keyfactor Command supports multiple custom-built PAM providers are available on the Keyfactor GitHub:
A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. steps (see ). Keyfactor Command supports multiple custom-built PAM providers are available on the Keyfactor GitHub:
PAM providers can either be local (server side) or remote (client side). When configured locally, the configuration information to connect to the PAM provider exists on the Keyfactor Command server and the PAM provider must be routable from the Keyfactor Command server (for example, on the same network) to retrieve secret information. When configured remotely, the configuration information to connect to the PAM provider exists on the Keyfactor Universal Orchestrator![]() The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. managing the certificate stores using the PAM provider and the PAM provider must be routable from the Universal Orchestrator
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. managing the certificate stores using the PAM provider and the PAM provider must be routable from the Universal Orchestrator![]() Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores..
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores..
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
 Adding or Modifying a PAM Provider
Adding or Modifying a PAM Provider
The PAM provider configuration can be edited at any time, even if it is used on existing records.
To define a new PAM provider or modify an existing one:
- In the Management Portal, browse to System Settings Icon
 > Privileged Access Management.
> Privileged Access Management. - On the PAM Providers page, click Add to create a new provider, or, to modify an existing provider, double-click the provider, right-click the provider and choose Edit from the right-click menu, or highlight the row in the providers grid and click Edit at the top of the grid.
-
In the PAM Providers dialog, check the Remote Provider box if you are adding a PAM provider for a PAM extension installed on a Universal Orchestrator.
A remote PAM provider generally exists outside the local network of the Keyfactor Command server. This option allows you to specify the secret information in Keyfactor Command in the same way as you would with a local PAM provider without needing to enter PAM provider configurations in Keyfactor Command (other than a base remote provider link). The PAM provider configuration information is, instead, supplied in the orchestrator's PAM manifest (see Installing Custom PAM Provider Extensions). Remote PAM providers are only supported for use with certificate stores and the Keyfactor Universal Orchestrator version 10.0 or greater.
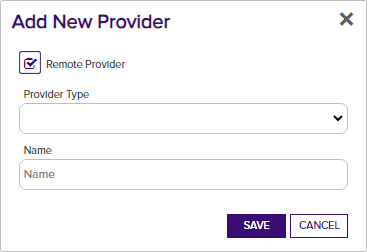
Figure 393: Remote PAM Provider
-
Select a Provider Type in the dropdown. This is the name of the software vendor that provides your Privilege Access Management solution. This field cannot be modified on an edit.
Note: If a provider type does not already exist for the PAM provider you are adding, you will need to create a new supported type before completing this step (see Installing Custom PAM Provider Extensions). -
In the Name field, enter the name for the PAM provider. This name is used to identify the PAM provider throughout Keyfactor Command.
Important: The name you give to your PAM provider in Keyfactor Command must match the name of the PAM provider as referenced in the manifest.json file (see Installing Custom PAM Provider Extensions). - The remainder of the fields in the dialog will vary depending on the provider type selected. If you checked Remote Provider, no further configuration is needed in this dialog. For example:
 CyberArk Extension (Central Credential Provider)
CyberArk Extension (Central Credential Provider)- Application ID: The name/ID of the application created for Keyfactor Command.
- CyberArk Host and Port: The hostname
 The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). or IP address where CyberArk is hosted, including port. Do not include http/https.
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). or IP address where CyberArk is hosted, including port. Do not include http/https. CyberArk API Site: The web server site name to which CyberArk has been deployed. By default, this is AIMWebService.

Figure 394: Create CyberArk Provider
 Delinea Extension
Delinea Extension- Secret Server URL: The URL to the Secret Server vault instance, including port number if applicable (e.g. https://websrvr38.keyexample.com/SecretServer).
- Secret Server Username: The username of the user that will be used to connect to SecretServer.
Secret Server Password: The password of the user that will be used to connect to SecretServer.
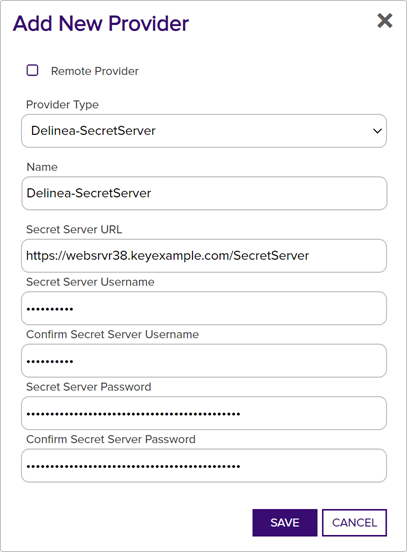
Figure 395: Create Delinea PAM Provider
 HashiCorp Extension
HashiCorp Extension- Vault Host: The URL to the vault instance, including port number if applicable (e.g. https://websrvr35.keyexample.com:8200).
- Vault Token: The access token for the vault (assuming Kerberos authentication is not used).
KV Engine Path: The path to the vault secrets. The default is v1/secret/data.

Figure 396: Create HashiCorp PAM Provider
- Click Save to save the provider.
 Deleting a PAM Provider
Deleting a PAM Provider
To delete a provider, highlight the row in the providers grid and click Delete at the top of the grid or right-click the provider in the grid and choose Delete from the right-click menu.